
Disaster recovery plan hints
A disaster recovery plan (DRP) is a critical component of any small business' contingency planning. A disaster, whether natural or man-made, can disrupt the normal operations of a business and…[...]
Read Full Recipe
A disaster recovery plan (DRP) is a critical component of any small business' contingency planning. A disaster, whether natural or man-made, can disrupt the normal operations of a business and…[...]
Read Full Recipe
What is chatgpt? ChatGPT is a conversational artificial intelligence language model developed by OpenAI. It uses the GPT (Generative Pretrained Transformer) architecture, which is a type of neural network designed…[...]
Read Full Recipe
Business continuity plan (BCP) is a document that outlines how an organization will continue its critical functions in the event of a disruption. The goal of a BCP is to…[...]
Read Full Recipe
On premises e documents management app: An on-premises electronic document management (EDM) app is a software solution that is installed, and run on a local server or servers within your…[...]
Read Full Recipe
Password Length: Passwords must be at least 8 characters in length. Complexity: Passwords must contain a combination of upper and lower case letters, numbers, and special characters. Password Expiration: Passwords…[...]
Read Full Recipe
Recursive DNS (Domain Name System) is a method by which a DNS resolver (such as a DNS server or client application) queries multiple DNS servers in order to resolve a…[...]
Read Full Recipe
Cybersecurity is the practice of protecting internet-connected systems, including hardware, software, and data, from attack, damage, or unauthorized access. It involves a combination of technologies, processes, and practices designed to…[...]
Read Full Recipe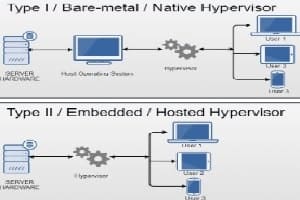
Hyper-V is a Microsoft virtualization technology that allows you to create and run virtual machines (VMs) on a single physical server. It is a native hypervisor that enables you to…[...]
Read Full Recipe
A corporate network is a type of computer network that connects the devices and systems within an organization, such as a business or government agency. This network is used to…[...]
Read Full Recipe
Introducing Meta: A Social Technology Company on October 28,2021 at Connect 2021, CEO Mark Zuckerberg introduced Meta, which brings together their apps and technologies under one new company brand. Meta’s…[...]
Read Full Recipe